How to Perform an Application Vulnerability Assessment
Application Vulnerability Assessment
Picking the right vulnerability scanning tool is often a tough job for a practitioner. The varied coverage and diversity of tools often make it difficult for him to pick the right tool.
This article gives you an insight into application vulnerability evaluation and helps you choose the right database and scanning tool.
Is It Necessary to Perform An Application Vulnerability Assessment?
Because of its different offered benefits, a uniformly expanding cluster of application is relocating to the cloud. Such a step needs to be deliberately taken due to the open nature of the Cloud.
Further, because of the coordinated improvement cycle that applications follow, their security level probably won't be the most ideal one, showing different sorts of vulnerability. All things considered, to simplify application relocation and runtime provisioning, this article throws light on three principle commitments.
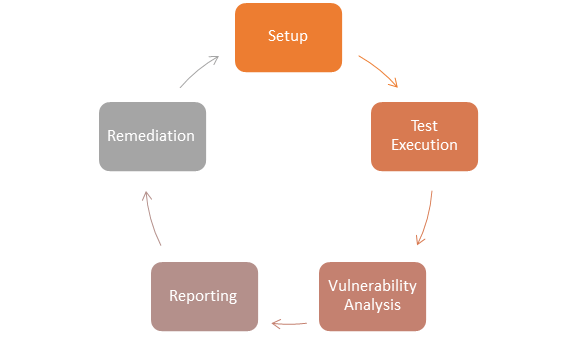
How the Vulnerability Assessment Is Conducted
Linking the application lifecycle with vulnerability management is the first step of vulnerability assessment. It helps in highlighting the real moments of performing application vulnerability assessment.
Second, it examinations the cutting edge open-source instruments and databases in order to empower designers about settling for an option that fits in with their knowledge and experience.
In this sense, finding such vulnerabilities will make it easier to secure applications in advance or when you finish relocating them to the cloud. The examination is functionally very rich and covers different angles and functional criteria.
Third, it investigates the idea that vulnerability assessment software should be coordinated effectively to arrive at the maximum vulnerability coverage, both regarding expand and expansiveness. At long last, this article finishes up with certain difficulties that present vulnerability instruments and databases need to face to raise their value and level of applicability.
Vulnerability assessment tools help in identifying vulnerabilities in various application parts. Likewise audit tools help in identifying code bugs that the hackers can exploit.

